SOC 2 (System and Organization Controls 2) compliance is a standard developed by the American Institute of CPAs (AICPA) that helps organizations ensure the security, availability, processing integrity, confidentiality, and privacy of their customers' data.
Compliance with SOC 2 is based on five trust principles: security, availability, processing integrity, confidentiality, and privacy. To be SOC 2 compliant, an organization must demonstrate that it has adequate controls and processes in place to ensure that these principles are met.
The SOC 2 audit is conducted by a third-party auditor who examines the controls and processes that an organization has in place to meet the trust principles. The auditor then issues a report that outlines the organization's level of compliance with the SOC 2 standard.
SOC 2 compliance is particularly relevant to technology companies that provide services to other organizations, such as cloud computing providers or software as a service (SaaS) companies. However, any organization that collects or processes customer data can benefit from SOC 2 compliance.
SOC 2 Compliance Checklist for the Software Development Lifecycle
Some of the SOC 2 prerequisites that are related to the software development lifecycle (SDLC) include:
- Secure coding practices: SOC 2 requires that organizations implement secure coding practices to ensure that their software is developed securely from the outset. Input validation, output encoding, access control, and error handling are all included in this process.
- Change management: SOC 2 requires that organizations have a well-defined change management process in place for their software development lifecycle. This process should include requirements for testing, peer review, and approval of code changes, as well as procedures for documenting and tracking changes.
- Vulnerability management: SOC 2 requires that organizations have a formal vulnerability management program in place to identify, assess, and remediate vulnerabilities in their software. This includes conducting regular vulnerability scans and penetration testing, as well as establishing procedures for addressing identified vulnerabilities.
- Access controls: SOC 2 requires that organizations have strong access controls in place to ensure that only authorized individuals can access their software development environment. This includes practices such as strong authentication and authorization controls, as well as monitoring and logging of access.
- Data security: SOC 2 requires that organizations have appropriate data security measures in place to protect the confidentiality, integrity, and availability of customer data. This includes practices such as encryption of sensitive data, access controls to limit who can view or modify data, and monitoring and logging of data access and changes.

These are just a few examples of the SOC 2 prerequisites that are relevant to the software development lifecycle. The specific prerequisites that an organization must meet will depend on its unique situation and the nature of its business operations.
SOC 2 Audit: Automating SOC 2 Compliance Requirements
Achieving SOC 2 compliance can be a daunting task if you are not armed with the right tools and processes to facilitate the audit as early as possible in your software development processes. Here, we’ve compiled a list of tools aimed at facilitating each of the prerequisites mentioned earlier.
Facilitating Secure Coding Practices
Code analytics tools such as SonarQube or Snyk can play a vital role in facilitating secure coding practices, which is one of the requirements for SOC 2 compliance. By automating the process of identifying vulnerabilities in your code, these tools help minimize the risk of security breaches, optimize coding practices, and ultimately shorten the time required for code reviews.
With SonarQube, for example, you can analyze your codebase for vulnerabilities, bugs, and code smells in real time. The tool provides detailed reports and metrics, including a code coverage report, which can help you identify areas of your codebase that require additional testing. Furthermore, SonarQube integrates with the most popular development environments and source code management tools, allowing you to automate code analysis and review as part of your development workflow.
Snyk is another powerful code analytics tool that helps identify vulnerabilities in your codebase by scanning your code and open-source dependencies for potential security flaws. Snyk can also integrate with your development environment and provide continuous monitoring, making it easier to identify and remediate vulnerabilities as they arise.
By implementing these tools as part of your software development process, you can minimize the risk of security breaches, improve the overall quality of your codebase, and meet the secure coding practices requirement for SOC 2 compliance.
Automating Change Management and Assessing Overall DevOps Practices
By using Keypup's Audit and Compliance Dashboard to automate compliance tracking and reporting, software companies can save significant time and effort in the SOC 2 compliance process. Some specific time-saving benefits include:
- Automated tracking of pull requests (PRs) and projects compliance status in real time, reducing the need for manual tracking and reporting
- Instant visibility into the compliance status of all PRs and projects, allowing for quick identification and resolution of compliance issues
- Streamlined compliance workflows through automated tracking of green build status and peer reviews before merging, reducing the need for manual oversight and intervention
- Elimination of time-consuming manual documentation processes through automated logging and reporting of compliance exceptions
- Overall reduction in the time and effort required for compliance reporting and audit preparation, allowing teams to focus on core business activities and development priorities
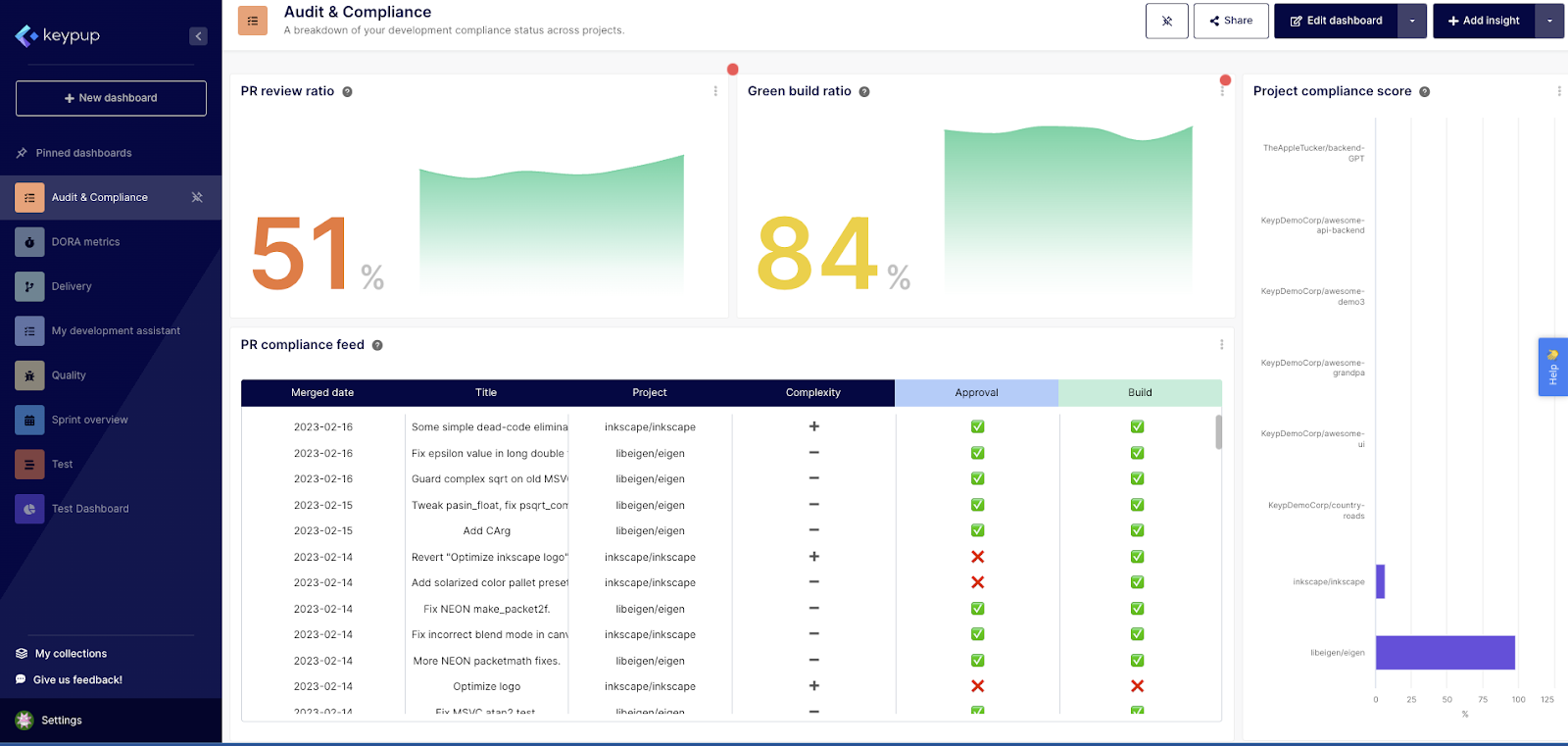
In summary, by using Keypup's Audit and Compliance Dashboard to automate compliance tracking, software companies can save valuable time and resources, streamline compliance workflows, and ultimately achieve SOC 2 compliance more efficiently.
Vulnerability Management Softwares
Vulnerability management tools such as Trivy or Detectify can significantly help software companies achieve SOC 2 compliance by providing an automated and efficient way of identifying and addressing vulnerabilities. Here are some ways these tools can assist with SOC 2 compliance:
- Scan for vulnerabilities: These tools can scan your environment, including cloud and Kubernetes clusters, to identify potential vulnerabilities such as misconfigurations, outdated software versions, and known security risks.
- Prioritize risks: The tools can help you prioritize identified risks based on their severity and impact on your organization's security and data privacy.
- Automate vulnerability management: These tools can automate the process of identifying and addressing vulnerabilities, reducing the risk of human error and minimizing the time required to remediate vulnerabilities.
- Provide insights and recommendations: These tools can provide valuable insights and recommendations to improve your security posture and ensure compliance with SOC 2 requirements.
By using vulnerability management tools, software companies can save significant time and effort in identifying and addressing potential vulnerabilities, thereby helping them achieve SOC 2 compliance more efficiently.
Multi-Layer Access Control Management
ForgeRock, Okta, GCP IAM, AWS IAM, or Azure IAM are identity and access management (IAM) solutions that help simplify the process of managing access control, which is a critical component of SOC 2 compliance. By using these tools, organizations can set up centralized authentication and authorization processes, manage user identities, and monitor user access to resources. These tools also provide features such as multi-factor authentication (MFA), single sign-on (SSO), and password management, which can help organizations comply with access control requirements under SOC 2.
However, for early-stage startups or organizations with limited resources, implementing such IAM solutions can be challenging due to the high costs and complex setup process. In such cases, here are some of the steps to access control management:
- Conduct an access control review and identify your organization's access control requirements.
- Develop an access control policy that outlines your organization's access control objectives and requirements.
- Develop access control procedures that define how access control will be implemented and managed.
- Establish a process for granting and revoking access to resources, including user account creation and termination procedures.
- Implement technical controls such as password policies, MFA, and role-based access control (RBAC).
- Monitor and review access control procedures and practices on an ongoing basis to ensure compliance with your organization's policies and procedures.
By following these steps, organizations can establish and maintain effective access controls, which is a key component of SOC 2 compliance, without the need for IAM solutions.
Data Security Enhancement
Data protection solutions such as Zscaler, Palo Alto or GCP Data Loss Prevention are designed to provide robust data security and help organizations adhere to strict data protection regulations like SOC 2. These tools help ensure data security in several ways:
- Secure data transfer: Data protection solutions offer secure channels for data transfer, which minimizes the risk of data loss or theft during transmission.
- Real-time monitoring: These tools provide real-time monitoring of network traffic and data usage, enabling you to identify and respond to suspicious activities quickly.
- Advanced Threat Protection: Data protection solutions use advanced threat detection and prevention technologies like machine learning and behavioral analysis to identify and block potential threats.
- Data loss prevention: These tools also help prevent data loss by encrypting sensitive data, implementing access controls and monitoring data movement to prevent unauthorized access and data exfiltration.
By implementing data protection solutions, organizations can strengthen their data security posture, meet regulatory requirements, and achieve SOC 2 compliance.
SOC 2 compliance can often seem like a daunting and stressful task, but with the right tools and processes, it doesn't have to be. By following a step-by-step guide and implementing automated solutions, achieving SOC 2 compliance can be much easier and less stressful than you might expect.
One of the key benefits of automating SOC 2 compliance requirements is that it can significantly reduce the time and effort required to prepare for an audit. By implementing tools such as SonarQube, Snyk, Keypup's Audit and Compliance Dashboard, and Trivy, organizations can streamline their compliance workflows, automate compliance tracking and reporting, and identify vulnerabilities in their codebase more efficiently.
Moreover, automating SOC 2 compliance can also help in improving the overall quality of an organization's software development process while minimizing the risk of security breaches and enhancing the overall quality of their codebase, which can lead to better performance, fewer bugs, and a more positive user experience.
While achieving SOC 2 compliance is undoubtedly an important goal for any organization that collects or processes customer data, it doesn't have to be a stressful or overwhelming experience. By following this guide and implementing the right tools and processes, organizations can achieve SOC 2 compliance more efficiently and effectively than ever before. So don't be intimidated by the SOC 2 compliance process — with the right approach, you can achieve compliance with confidence. Start with Keypup’s Audit and Compliance Dashboard today!